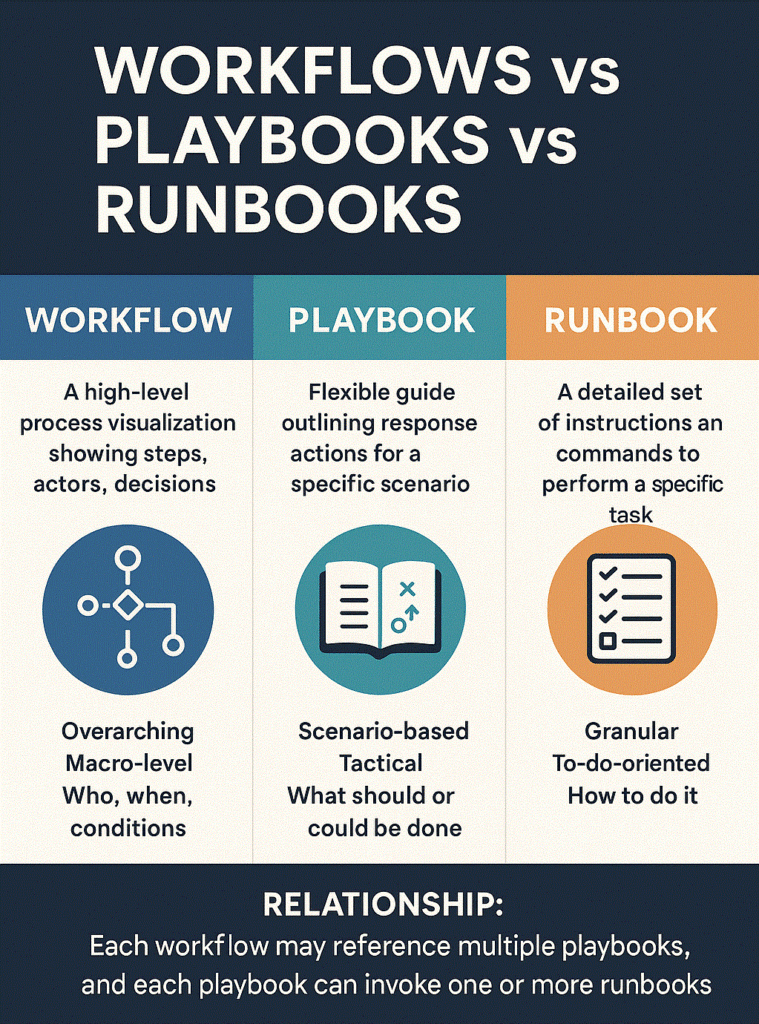
In cybersecurity, the terms playbook, runbook, and workflow are often used interchangeably—but they have distinct meanings. Here’s a detailed breakdown to help you clearly understand their differences, relationships, and practical use.
Contents
- 1 🧩 Overview Table
- 2 🔄 What is a Workflow?
- 3 📘 What is a Playbook?
- 4 🔧 What is a Runbook?
- 5 🔁 How They Work Together
- 6 ⚙️ Related Concepts
- 7 🛡 Example in Action: Phishing Response
- 8 🎯 Summary
- 9 Example
- 10 🎯 Incident Scenario: Suspicious PowerShell Execution on an End-User Laptop
- 11 📎 Summary: Mapping All Three Together
🧩 Overview Table
| Term | Purpose | Granularity | Used By | Level |
|---|---|---|---|---|
| Workflow | High-level process flow (visual/logical) | Macro / Process-level | Security teams, architects | Strategic |
| Playbook | Prescriptive guide for handling scenarios | Scenario-based | SOC, IR, threat hunters | Tactical |
| Runbook | Step-by-step technical instructions | Task-based | Analysts, engineers | Operational |
🔄 What is a Workflow?
Definition:
A workflow is a high-level visual or logical sequence of steps that describes how a process should be carried out—from start to finish. It focuses on who does what, when, and under what conditions.
Characteristics:
- Often visual (flowcharts, diagrams)
- Includes decision points
- Used for planning, training, and automation design
Example:
An alert triggers in Sentinel → Analyst triages alert → Confirms phishing → Escalates to IR → IR isolates host and resets credentials
📘 What is a Playbook?
Definition:
A playbook provides a repeatable response guide to a known threat scenario. It includes logic, decision trees, conditions, and actions—but does not always include the literal steps for execution.
Characteristics:
- Tactical, scenario-specific
- Contains threat context and response paths
- May link to multiple runbooks
- Often used in SOAR tools
Example:
Phishing Email Playbook:
- Identify reported email
- Validate indicators
- Determine scope
- Contain impact
- Notify users
- Feed IOCs into threat intelligence platform
🔧 What is a Runbook?
Definition:
A runbook contains detailed, often technical instructions that guide analysts or automation tools through performing a specific task.
Characteristics:
- Very procedural
- Step-by-step format
- May include CLI commands, GUI clicks, or API calls
- Can be manual or automated (via SOAR)
Example:
Reset Compromised User Runbook:
- Disable user in Azure AD
- Remove active sessions
- Reset password
- Notify SOC channel
- Document in ticket
🔁 How They Work Together
Think of it like a pyramid:
Workflow (Top-Level Overview)
└── Playbook (Scenario-Specific Logic)
└── Runbook(s) (Executable Task Details)
Each workflow may involve multiple playbooks, and each playbook can invoke one or more runbooks to perform exact steps.
⚙️ Related Concepts
| Term | Description |
|---|---|
| Standard Operating Procedure (SOP) | General operational process not tied to a threat or system |
| Automation Playbooks | SOAR workflows that integrate playbooks and runbooks in tools like Sentinel or Splunk |
| Decision Trees | Logic used within playbooks to guide analyst decisions |
| Escalation Matrix | Defines who gets involved and when in a workflow or playbook scenario |
🛡 Example in Action: Phishing Response
| Element | What It Includes |
|---|---|
| Workflow | Full lifecycle: from detection → triage → response → review |
| Playbook | Steps to respond to phishing: validate, scope, contain |
| Runbook | 1. Analyse headers 2. Sandbox URL 3. Block sender address |
🎯 Summary
| Term | Focus | Example |
|---|---|---|
| Workflow | End-to-end process | Incident detection to remediation |
| Playbook | Scenario response | How to handle a phishing alert |
| Runbook | Task execution | How to reset a compromised password |
Example
Here’s a real-world incident response example that shows how a workflow, playbook, and runbook all work together to resolve a malicious PowerShell execution alert — such as one detected by Microsoft Defender for Endpoint or Sentinel.
🎯 Incident Scenario: Suspicious PowerShell Execution on an End-User Laptop
1️⃣ Workflow – High-Level Process Flow
The workflow outlines the entire incident lifecycle from detection to resolution:
📍 Alert Triggered (Defender/Sentinel)
↓
🕵️ Triage by SOC Analyst
↓
📌 Confirm Malicious Behaviour (e.g. obfuscated PowerShell)
↓
🚨 Escalate to Incident Response Team
↓
🔒 Contain Host (via EDR or network isolation)
↓
🛠 Execute Response Playbook
↓
🧼 Eradicate Threat + Perform Root Cause Analysis
↓
🧾 Run Post-Incident Review & Document Lessons
This workflow ensures consistent handling and assigns ownership per step.
2️⃣ Playbook – Tactical Response for “Suspicious PowerShell” Alert
This playbook provides the logic and decision paths to follow based on the scenario.
🔧 PowerShell Execution Detection Playbook
| Step | Description |
|---|---|
| 1. Validate Alert | Confirm script behaviour (e.g. Invoke-Expression, encoded base64) |
| 2. Check Scope | Was it executed on one host or multiple? Check for lateral movement |
| 3. Investigate File/Script | Perform static analysis (without execution) and decode any obfuscation |
| 4. Contain Endpoint | Isolate host using Defender for Endpoint or remove it from the network |
| 5. Identify Payload | Determine if it downloaded additional files or exfiltrated data |
| 6. Block IOCs | Update firewall, EDR, or email filters to block malicious domains or hashes |
| 7. Notify Teams | Send alerts to IR team and relevant business owners |
| 8. Escalate or Close | If confirmed malicious, escalate to IR; otherwise, close and document as benign |
3️⃣ Runbooks – Technical Task Scripts
The runbook provides precise, actionable instructions for technical tasks within the playbook.
🛠️ Runbook A: Decode Obfuscated PowerShell Script
# 1. Assign the base64 string
$b64 = "JAB1AHIAbAA9ACcAaAB0AHQAcAA6AC8ALwBtAGE..."
# 2. Decode the script safely
$decoded = [System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($b64))
# 3. Output the result for manual review
Write-Output $decoded
# 4. Save to log for documentation
$decoded | Out-File -FilePath "C:\IR\decoded_script.txt"
🛠️ Runbook B: Contain Endpoint via Defender for Endpoint
# Use Microsoft Defender API or portal
1. Locate endpoint ID in MDE portal
2. Select “Isolate Device”
3. Choose "Full Network Isolation"
4. Add exceptions for IR team IPs if needed
🛠️ Runbook C: Block Domain Using Firewall (e.g. Palo Alto, NPM)
1. Log in to the firewall console
2. Navigate to “Threat → Block List”
3. Add domain: malicious.evil.com
4. Apply policy and push config
📎 Summary: Mapping All Three Together
| Layer | Tool or Format | Example in This Scenario |
|---|---|---|
| Workflow | Flowchart or diagram | End-to-end incident lifecycle |
| Playbook | SOAR/Markdown/SharePoint | PowerShell execution response plan |
| Runbook | CLI scripts, GUI steps, API | Decoding script, isolating host, blocking IOCs |