Contents
🛡️ What is EDR (Endpoint Detection and Response)?
Endpoint Detection and Response (EDR) is a cybersecurity technology designed to detect, investigate, and respond to suspicious activity on endpoint devices such as laptops, desktops, servers, and mobile devices.
🔍 Why is EDR Important?
Traditional antivirus tools rely on known signatures to block malware. However, modern threats like fileless malware, ransomware, and insider attacks often evade traditional defences.
EDR steps in by providing:
- Real-time visibility into endpoint behaviour
- Detection of advanced threats
- Rapid investigation and response tools
🧠 How EDR Works
EDR solutions continuously monitor and collect activity data from endpoints. When suspicious behaviour is detected (e.g. unusual PowerShell activity, lateral movement, or privilege escalation), EDR systems:
- Alert analysts
- Provide a timeline of events
- Allow containment (e.g. isolating a host)
- Support forensic investigation
This allows security teams to hunt threats proactively and minimise dwell time.
🔧 Core Features of EDR
| Feature | Description |
|---|---|
| Continuous Monitoring | Tracks endpoint activity 24/7 |
| Threat Detection | Uses AI/ML and behavioural analytics |
| Incident Response | Enables remote isolation, memory dumps, or process kills |
| Forensic Data | Provides historical data for investigation |
| Threat Hunting | Analysts can query endpoint telemetry to find hidden threats |
| Integration | Connects with SIEM, SOAR, and threat intelligence feeds |
🖥️ What Devices Does EDR Cover?
- Windows, macOS, and Linux endpoints
- Cloud workloads (AWS, Azure, GCP)
- Virtual machines
- Containers
- Mobile devices (in some platforms)
🔄 EDR vs Antivirus
| Feature | Traditional Antivirus | EDR |
|---|---|---|
| Signature-Based | ✅ Yes | ⚠️ Limited |
| Behavioural Analysis | ❌ No | ✅ Yes |
| Real-Time Response | ❌ No | ✅ Yes |
| Threat Hunting | ❌ No | ✅ Yes |
| Memory/Process Visibility | ❌ No | ✅ Yes |
EDR doesn’t replace antivirus — it extends and strengthens endpoint security.
🛠️ Examples of Popular EDR Tools
- CrowdStrike Falcon
- Microsoft Defender for Endpoint
- SentinelOne
- VMware Carbon Black
- Sophos Intercept X
🔒 EDR in a Cybersecurity Stack
EDR is often part of a defence-in-depth strategy, sitting alongside:
- Firewalls
- SIEM (Security Information and Event Management)
- SOAR (Security Orchestration, Automation, and Response)
- Threat Intelligence Platforms
- MDR/XDR services
🧠 Summary
EDR is a vital cybersecurity layer that empowers security teams to detect, investigate, and respond to threats targeting endpoints. It closes the gap left by traditional antivirus and helps reduce the impact of breaches by responding in real-time.
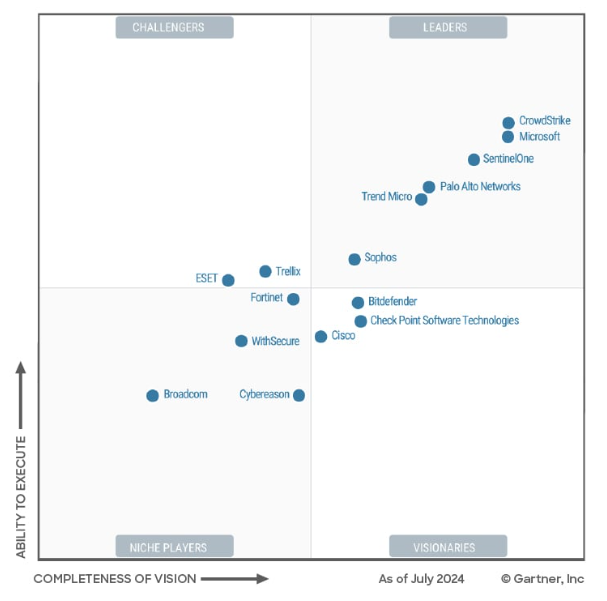
🔝 Top Enterprise EDR Tools
| EDR Tool | Why It’s Best for Enterprise |
|---|---|
| CrowdStrike Falcon | Cloud-native, lightweight agent, strong behavioural AI detection, threat intelligence integration, used widely in finance, healthcare, and tech. |
| Microsoft Defender for Endpoint | Deep integration with Windows/365/Azure, powerful if already in the Microsoft ecosystem, strong analytics and automation via Defender XDR. |
| SentinelOne Singularity | Autonomous AI-based response, great for automated remediation, strong container and Linux coverage, ideal for hybrid environments. |
| Sophos Intercept X with XDR | Strong ransomware protection, deep learning engine, integrates with firewalls and email gateways, suitable for mid-to-large orgs. |
| Trend Micro Vision One | Unified XDR platform, strong in user-behaviour analytics and layered security, works well in multi-cloud environments. |
| Trellix (formerly McAfee + FireEye) | Strong threat intel (FireEye heritage), wide coverage across OS and devices, good for regulated sectors. |
| Cybereason Defense Platform | Highly visual attack graphs, strong behavioural correlation, and multi-stage detection ideal for SOC teams. |
| VMware Carbon Black Cloud | Strong for behavioural EDR and application control, integrates tightly with vSphere/ESXi, good for virtualised data centres. |
| Bitdefender GravityZone Elite | Lightweight, strong heuristics, rich dashboard, suitable for smaller enterprises or distributed teams. |
| Cisco Secure Endpoint (AMP) | Good network+endpoint correlation, ideal if already using Cisco ecosystem (Umbrella, Firepower, etc.). |