The Diamond Model of Intrusion Analysis is a framework used by security analysts to better understand, categorise, and respond to cyber attacks. Instead of looking at isolated events, the model maps out the relationships between different components of an intrusion, helping teams see the bigger picture and improve their threat intelligence.
Contents
The Four Core Features
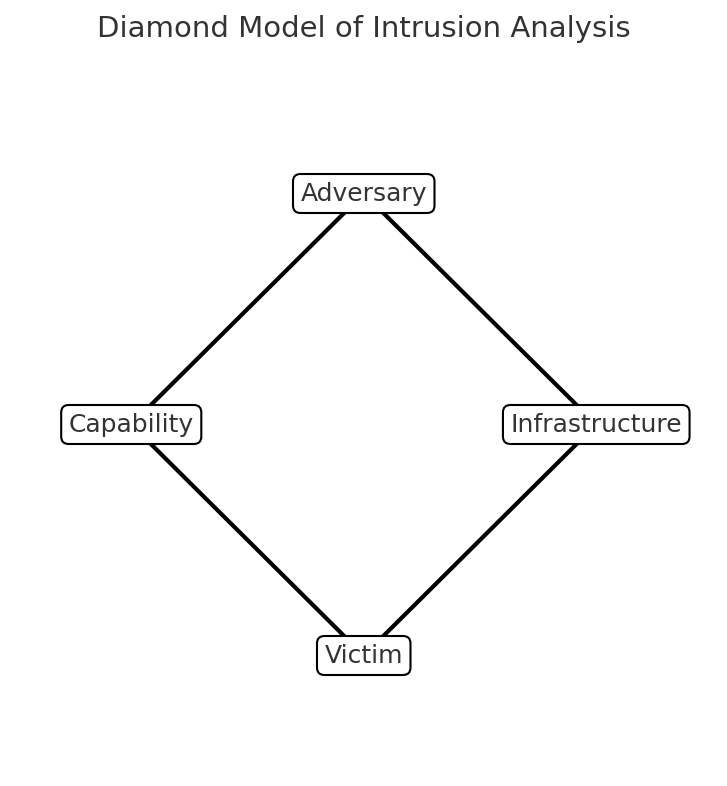
At its centre, the Diamond Model highlights four key features of any intrusion:
- Adversary – The attacker behind the operation. This could be an individual, a group, or a nation-state.
- Infrastructure – The systems and services the adversary uses to launch and control the attack, such as command-and-control servers, phishing domains, or exploited cloud services.
- Capability – The tools and techniques deployed by the attacker, including malware, exploits, or social engineering.
- Victim – The target of the attack. This could be an organisation, a system, or a specific individual.
These four elements are connected like a diamond, showing how each component relates to the others. For example, an adversary uses a capability through an infrastructure to compromise a victim.
Enriching the Model
The framework can be expanded by adding context such as:
- Technology – What platforms, software, or protocols were involved.
- Timeline – When each activity occurred.
- Social/Political Factors – Why the attack might have taken place.
This extra detail helps build a more complete picture of an adversary’s behaviour.
Why It Matters
The Diamond Model is useful because it:
- Improves analysis – Helps security teams connect disparate events into a coherent attack story.
- Supports threat hunting – By looking at one element (e.g. an IP address), analysts can pivot to find related capabilities, adversaries, or victims.
- Drives intelligence sharing – Provides a structured way to share intrusion information between organisations.
- Strengthens defence – Understanding the attacker’s methods enables stronger detection, prevention, and response strategies.
Example in Practice
Imagine you discover a phishing email targeting your company. By applying the Diamond Model:
- Victim – Employees in your finance department.
- Capability – A credential-harvesting phishing kit.
- Infrastructure – A malicious domain registered to look like your payment processor.
- Adversary – A financially motivated cybercrime group.
Linking these points gives you a clear picture of the attack, allowing you to block the domain, hunt for other related indicators, and brief staff on the specific threat.
Conclusion
The Diamond Model of Intrusion Analysis provides a structured way to think about attacks. By mapping adversary, infrastructure, capability, and victim, organisations can improve their incident response, build stronger intelligence, and anticipate future threats more effectively.