In today’s interconnected digital landscape, APIs and web applications form the backbone of modern software systems. Ensuring their security is not just a technical requirement but a critical business imperative that protects data, maintains user trust, and ensures regulatory compliance.
Contents
Understanding the Security Landscape
Web applications and APIs face an evolving threat landscape where attackers constantly develop new techniques to exploit vulnerabilities. Security must be built into every layer of your application architecture, from the network perimeter to the application logic itself.
Core Security Principle: Security is not a one-time implementation but an ongoing process that requires continuous monitoring, updating, and improvement.
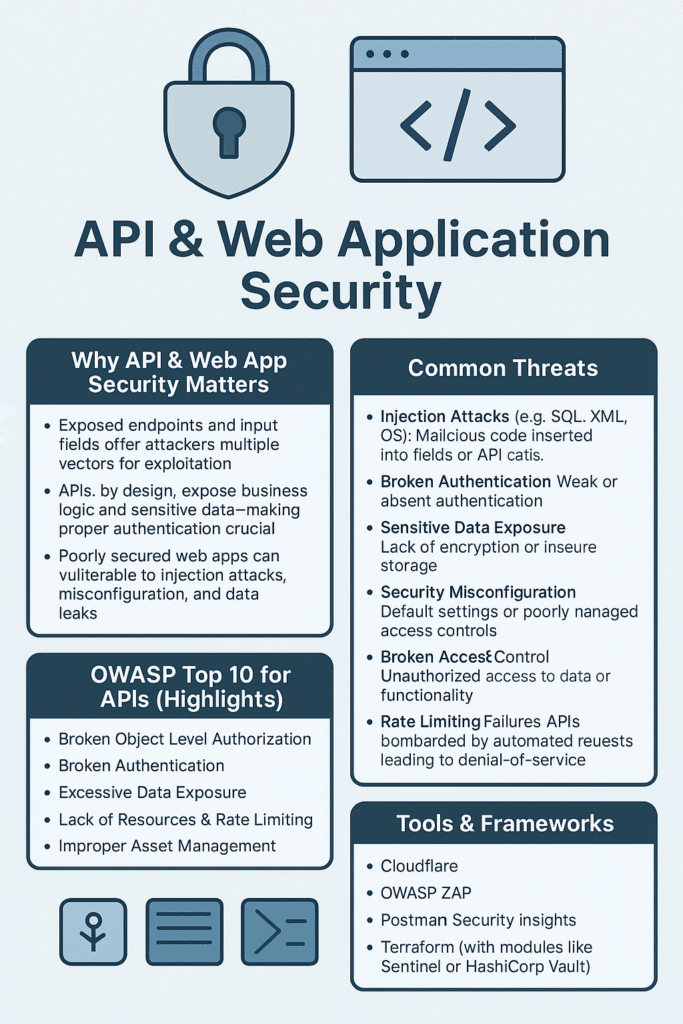
Common Security Threats
Injection Attacks
Injection vulnerabilities occur when untrusted data is sent to an interpreter as part of a command or query. Attackers can trick the interpreter into executing unintended commands or accessing unauthorized data. This includes SQL injection, NoSQL injection, and command injection attacks.
Authentication and Session Management Flaws
Broken authentication allows attackers to compromise passwords, keys, or session tokens, or exploit other implementation flaws to assume other users’ identities. This can lead to unauthorized access to sensitive data and functionality.
Cross-Site Scripting (XSS)
XSS flaws occur when applications include untrusted data in web pages without proper validation or escaping. Attackers can execute scripts in victims’ browsers, hijacking user sessions, defacing websites, or redirecting users to malicious sites.
Insecure Direct Object References
This vulnerability occurs when developers expose references to internal implementation objects, such as files, directories, or database keys. Without access control checks, attackers can manipulate these references to access unauthorized data.
Security Misconfiguration
Security misconfiguration is one of the most common issues, resulting from insecure default configurations, incomplete or ad hoc configurations, open cloud storage, misconfigured HTTP headers, and verbose error messages containing sensitive information.
API-Specific Security Considerations
Rate Limiting and Throttling
APIs are particularly vulnerable to abuse through automated attacks and denial of service attempts. Implementing rate limiting ensures that no single user or system can overwhelm your API with requests, maintaining availability for legitimate users.
API Authentication Methods
Modern APIs typically use token-based authentication systems. These include API keys for simple scenarios, OAuth 2.0 for delegated authorization, and JSON Web Tokens (JWT) for stateless authentication. Each method has its appropriate use cases and security considerations.
Input Validation and Data Sanitization
Every piece of data entering your API must be validated against expected formats, ranges, and types. This includes checking data types, string lengths, numeric ranges, and ensuring that data conforms to expected patterns.
Warning: Never trust client-side validation alone. Always perform server-side validation as attackers can easily bypass client-side controls.
Best Practices for Secure Development
Implement Defense in Depth
Security should be layered throughout your application. If one security control fails, others should still protect your system. This includes network security, application security, and data security measures working together.
Principle of Least Privilege
Users, processes, and systems should only have the minimum level of access necessary to perform their functions. This limits the potential damage from compromised accounts or components.
Secure Communication
All data transmission should be encrypted using TLS/SSL. This includes not just user-facing communications but also backend service-to-service communications. Ensure you’re using current TLS versions and strong cipher suites.
Best Practice: Always use HTTPS for all communications. HTTP should redirect to HTTPS, and consider implementing HTTP Strict Transport Security (HSTS) headers.
Error Handling and Logging
Proper error handling prevents information leakage that could aid attackers. Error messages shown to users should be generic, while detailed error information should be logged securely for debugging purposes. Ensure logs don’t contain sensitive information like passwords or tokens.
Regular Security Audits
Conduct regular security assessments including:
- Automated vulnerability scanning
- Manual penetration testing
- Code reviews focusing on security
- Dependency scanning for known vulnerabilities
- Configuration reviews
Compliance and Regulatory Considerations
Different industries and regions have specific security requirements. Common frameworks and regulations include:
- GDPR: For handling EU citizens’ data
- PCI DSS: For payment card processing
- HIPAA: For healthcare information
- SOC 2: For service organizations
- ISO 27001: International security standard
Understanding which regulations apply to your application is crucial for maintaining compliance and avoiding penalties.
Security Headers and Configurations
Implementing proper security headers provides an additional layer of defense against common attacks. Key headers include Content Security Policy (CSP) to prevent XSS attacks, X-Frame-Options to prevent clickjacking, and X-Content-Type-Options to prevent MIME sniffing attacks.
Incident Response Planning
Despite best efforts, security incidents may occur. Having a well-defined incident response plan ensures quick and effective action when breaches are detected. This plan should include:
- Clear roles and responsibilities
- Communication protocols
- Steps for containing and eradicating threats
- Recovery procedures
- Post-incident analysis processes
Conclusion
API and web application security is a multifaceted challenge requiring ongoing attention and investment. By understanding common threats, implementing best practices, and maintaining a security-first mindset throughout the development lifecycle, organizations can build robust applications that protect both their assets and their users’ data.
Remember: Security is everyone’s responsibility. From developers to operations teams to management, creating a culture of security awareness is essential for maintaining robust defenses against evolving threats.