Contents
- 1
- 2 🧠 Database Ports Reference Guide
- 2.1 🗄️ Relational Database Ports (SQL)
- 2.2 📦 NoSQL & Search Engine Ports
- 2.3 ☁️ Cloud SQL Service Ports (Typically Encapsulated)
- 2.4 🏠 Internal IP Address Ranges (RFC1918 & APIPA)
- 2.5 🔹 APIPA (Automatic Private IP Addressing)
- 2.6 🧭 Why This Matters
- 2.7 🔥 Top Exploited Ports (Attack Surface Awareness)
- 2.8 🛡️ Hardening Tips
- 2.9 🧰 Troubleshooting & Discovery Tools
- 2.10 🧱 OSI Model with Protocol Examples
A solid grasp of networking is fundamental for any cyber or infrastructure engineer. This page provides a quick reference to the most commonly used IP ports (including secure variants), a breakdown of TCP/UDP usage, and the key internal IP ranges — including the lesser-known APIPA.
🔌 Common IP Ports (with TCP/UDP and Protocol Reasoning)
| Port | Protocol | Service | TCP/UDP | Why TCP or UDP? |
|---|---|---|---|---|
| 20 | FTP Data | File Transfer Protocol | TCP | Reliable data delivery is essential for file integrity. |
| 21 | FTP Control | File Transfer Protocol | TCP | Commands must be reliably delivered and acknowledged. |
| 22 | SSH | Secure Shell | TCP | Requires secure, reliable, and ordered communication. |
| 23 | Telnet | Remote login (insecure) | TCP | Reliable terminal session needed for command execution. |
| 25 | SMTP | Email Sending | TCP | Ensures emails are delivered and acknowledged. |
| 53 | DNS | Domain Name System | TCP/UDP | UDP for fast lookups, TCP for larger queries like zone transfers. |
| 67 | DHCP Server | IP Address Assignment | UDP | Connectionless protocol; client/server discover each other via broadcast. |
| 68 | DHCP Client | IP Address Assignment | UDP | Same reason as above; used on the client side. |
| 69 | TFTP | Trivial File Transfer | UDP | Lightweight and simple, often used for booting devices. |
| 80 | HTTP | Web Traffic (Insecure) | TCP | Reliable page delivery and session tracking. |
| 110 | POP3 | Email Retrieval | TCP | Email contents must be delivered completely and in order. |
| 123 | NTP | Network Time Protocol | UDP | Fast and efficient; time sync doesn’t require reliable delivery. |
| 143 | IMAP | Email Retrieval | TCP | Enables complex mail handling that requires reliability. |
| 161 | SNMP | Network Management | UDP | Lightweight polling of devices — speed over reliability. |
| 162 | SNMP Trap | SNMP Notifications | UDP | Fast, fire-and-forget notifications. |
| 389 | LDAP | Directory Services | TCP/UDP | TCP for directory queries; UDP in some lightweight cases (less common). |
| 443 | HTTPS | Secure Web Traffic | TCP | Requires encryption and session persistence. |
| 445 | SMB | File Sharing (Windows) | TCP | File transfers and authentication must be reliable. |
| 514 | Syslog | Log Forwarding | UDP | Prioritises speed over delivery confirmation; logs may be sent in high volume. |
| 636 | LDAPS | Secure LDAP | TCP | Same as LDAP but encrypted — reliability still critical. |
| 993 | IMAPS | Secure IMAP | TCP | Secure, reliable retrieval of email. |
| 995 | POP3S | Secure POP3 | TCP | Same as POP3, but encrypted. |
| 1433 | MS SQL Server | Database | TCP | Reliable database connections are essential. |
| 1521 | Oracle DB | Database | TCP | Ensures consistent query/response handling. |
| 3306 | MySQL | Database | TCP | Structured data transactions require reliability. |
| 3389 | RDP | Remote Desktop Protocol | TCP/UDP | TCP for session reliability; UDP (optional) for multimedia optimisation. |
| 5060 | SIP (unencrypted) | VoIP Signalling | TCP/UDP | UDP common for VoIP efficiency; TCP for NAT traversal and reliability. |
| 5061 | SIP (TLS) | Secure VoIP Signalling | TCP | TLS encryption requires reliable, ordered transport. |
| 5900 | VNC | Remote GUI Access | TCP | Visual interface requires reliable transmission of screen data. |
| 8080 | HTTP-Alt | Web Proxy / Alt HTTP | TCP | Used for alternative or proxy HTTP traffic — reliability required. |
🔒 Secure Versions of Common Ports
| Insecure Service | Secure Equivalent | Port |
|---|---|---|
| HTTP | HTTPS | 443 |
| FTP | FTPS / SFTP | 990 / 22 |
| Telnet | SSH | 22 |
| POP3 | POP3S | 995 |
| IMAP | IMAPS | 993 |
| LDAP | LDAPS | 636 |
| SIP | SIP over TLS | 5061 |
🧠 Database Ports Reference Guide
🗄️ Relational Database Ports (SQL)
| Port | Service | Database | TCP/UDP | Why TCP or UDP? |
|---|---|---|---|---|
| 1433 | SQL Server | Microsoft SQL Server | TCP | Ensures reliable delivery of queries and results. |
| 1434 | SQL Browser Service | MS SQL (Discovery) | UDP | Used to locate named instances via broadcast. |
| 3306 | MySQL | MySQL | TCP | Handles transactional communication reliably. |
| 33060 | X Protocol | MySQL (JSON API) | TCP | Supports modern apps using MySQL as a document store. |
| 5432 | PostgreSQL | PostgreSQL | TCP | Maintains consistent, stateful client-server communication. |
| 1521 | Listener | Oracle DB | TCP | Directs client connections to appropriate Oracle services. |
| 2483 | Net8 (Unencrypted) | Oracle DB | TCP | Legacy Oracle connections. |
| 2484 | Net8 (Encrypted) | Oracle DB (TLS) | TCP | Secure alternative to port 2483. |
📦 NoSQL & Search Engine Ports
| Port | Service | Database | TCP/UDP | Why TCP or UDP? |
|---|---|---|---|---|
| 27017 | MongoDB | MongoDB | TCP | Handles document-based queries reliably. |
| 27018 | MongoDB Shard | MongoDB (Shard) | TCP | Internal shard communication. |
| 27019 | MongoDB Config | MongoDB (Cluster) | TCP | Cluster metadata management. |
| 6379 | Redis | Redis | TCP | In-memory key-value operations — TCP used for reliability. |
| 6380 | Redis TLS | Redis (Secure) | TCP | Secure alternative to 6379. |
| 9200 | REST API | Elasticsearch | TCP | Accepts HTTP requests for search and indexing. |
| 9300 | Cluster Comms | Elasticsearch | TCP | Internal node-to-node communication. |
| 9042 | Cassandra | Apache Cassandra | TCP | Reliable communication in a peer-to-peer distributed DB. |
| 5984 | CouchDB | Apache CouchDB | TCP | RESTful JSON document DB over HTTP. |
☁️ Cloud SQL Service Ports (Typically Encapsulated)
| Cloud Service | Underlying DB | Default Port | Notes |
|---|---|---|---|
| Amazon RDS | MySQL, PostgreSQL, SQL Server, Oracle | Varies (3306, 5432, 1433, 1521) | Same ports as on-prem; security groups control access. |
| Azure SQL Database | Microsoft SQL Server | 1433 | Must whitelist client IPs and enable firewall rules. |
| Google Cloud SQL | MySQL, PostgreSQL, SQL Server | Varies | Port access wrapped in secure connection using Cloud SQL Auth Proxy. |
🔐 Note: Cloud SQL services often use TLS by default and restrict access using IAM, firewalls, or client certificates rather than exposing raw database ports publicly.
🏠 Internal IP Address Ranges (RFC1918 & APIPA)
These IP ranges are not routable on the public internet and are used for internal networking:
🔹 Private IP Ranges
10.0.0.0 – 10.255.255.255 (Class A, /8)
172.16.0.0 – 172.31.255.255 (Class B, /12)
192.168.0.0 – 192.168.255.255 (Class C, /16)
These are often used in home networks, enterprise LANs, and VPNs. NAT (Network Address Translation) allows these private IPs to communicate externally.
🔹 APIPA (Automatic Private IP Addressing)
169.254.0.0 – 169.254.255.255
If a device cannot contact a DHCP server and has APIPA enabled, it assigns itself an IP in this range. This allows basic communication between devices on the same subnet but does not allow internet access.
🧭 Why This Matters
Understanding ports and addressing is critical for:
- Configuring firewalls and ACLs
- Diagnosing connectivity issues
- Monitoring network traffic for threats
- Securing services by enforcing encrypted communication
🔥 Top Exploited Ports (Attack Surface Awareness)
Ports commonly targeted by attackers:
| Port | Service | Reason It’s Targeted |
|---|---|---|
| 22 | SSH | Bruteforce attacks on remote logins. |
| 23 | Telnet | Insecure legacy service; credentials in plaintext. |
| 3389 | RDP | Popular for ransomware and brute-force entry. |
| 445 | SMB | Used in attacks like WannaCry (EternalBlue). |
| 80/443 | HTTP/HTTPS | Targeted for web app vulnerabilities. |
| 21 | FTP | Anonymous access & misconfigurations. |
| 53 | DNS | DDoS amplification, DNS tunnelling. |
🛡️ Hardening Tips
Include basic best practices for port/service security:
- Close unused ports.
- Use firewalls to restrict external access.
- Prefer secure alternatives (SSH over Telnet, HTTPS over HTTP).
- Monitor open ports with tools like
nmap,netstat, orss. - Use port knocking or VPNs for sensitive services like SSH and RDP.
- Enforce 2FA where possible for remote access services.
🧰 Troubleshooting & Discovery Tools
Quick CLI examples to discover or check open ports:
# Discover open ports on a target
nmap -sS -Pn 192.168.0.10
# List listening ports on a Linux host
ss -tuln
# Find which process is using a port
lsof -i :3306🧱 OSI Model with Protocol Examples
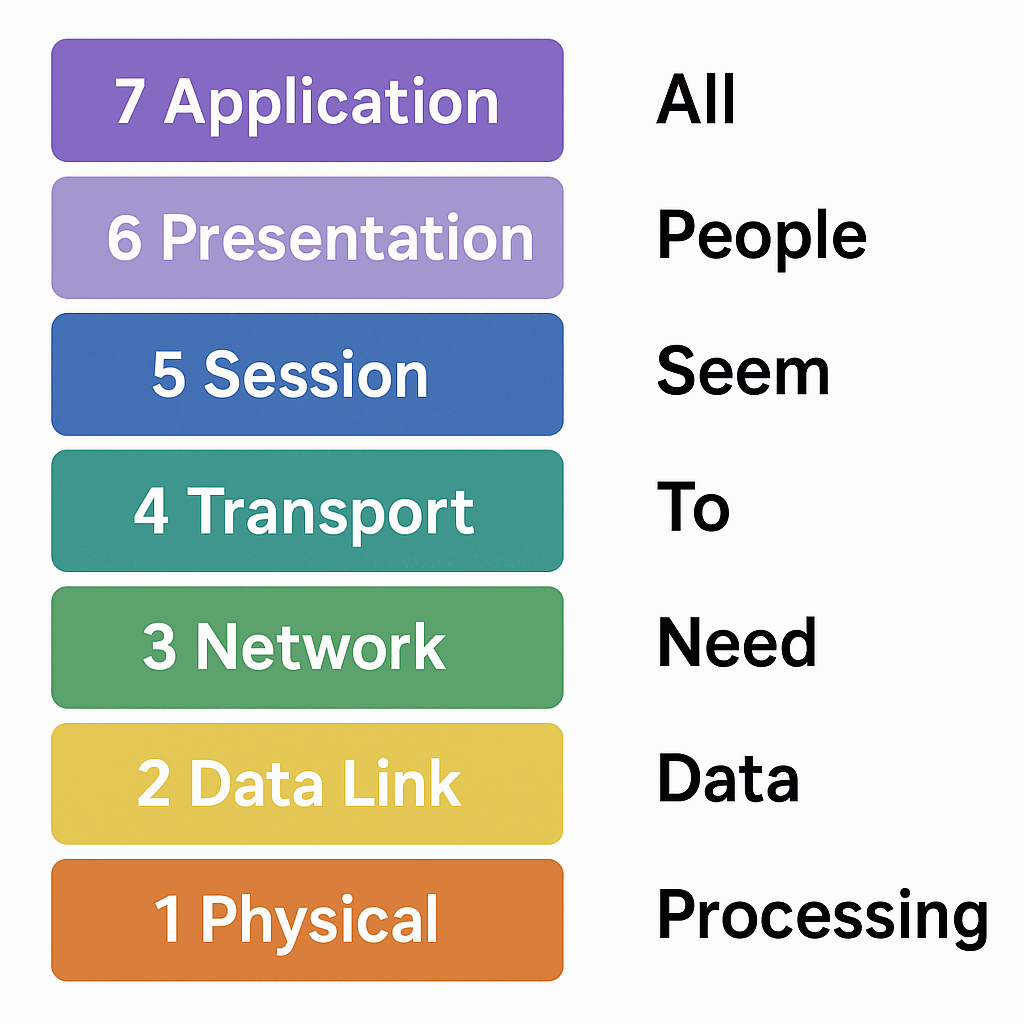
| Layer | Name | Example Protocols |
|---|---|---|
| 7 | Application | HTTP (80), DNS (53), SMTP (25) |
| 6 | Presentation | SSL/TLS |
| 5 | Session | NetBIOS, RPC |
| 4 | Transport | TCP, UDP |
| 3 | Network | IP, ICMP |
| 2 | Data Link | Ethernet, ARP |
| 1 | Physical | Cables, Switches |