Contents
🥇 Cybersecurity Programs by Priority (Foundational to Strategic)
| 🔢 | Program | Why Prioritise It First? |
|---|---|---|
| 1️⃣ | Incident Response Program 🚨 | Without a plan for detecting, containing, and responding to incidents, everything else is reactive. A clear IR process with playbooks is mission-critical. |
| 2️⃣ | Vulnerability Management Program 🔐 | Patching and vulnerability scanning closes common attack vectors. It’s a must-have for minimising exposure to known exploits. |
| 3️⃣ | Security Tooling & Automation Program 🛠️ | EDR, SIEM, logging and SOAR are key for visibility. Tooling enables detection and response — get it in place early and ensure data pipelines are flowing. |
| 4️⃣ | Detection Engineering Program ⚙️ | With telemetry flowing, begin tuning alerts, writing rules, and reducing false positives. Link detections to MITRE ATT&CK for coverage clarity. |
| 5️⃣ | Governance, Risk & Compliance (GRC) Program ⚖️ | Ensure there are policies, a risk register, and compliance alignment (e.g. ISO, SOC2). Stakeholders and auditors will ask for this early. |
| 6️⃣ | Security Awareness & Training Program 👨🏫 | Human error is often the root cause. Quick wins through phishing simulations and focused user training reduce risk dramatically. |
| 7️⃣ | Threat Intelligence Program 🔍 | As detections improve, TI enriches alerts and informs hunting. It also helps anticipate threats and prioritise based on what’s active. |
| 8️⃣ | Insider Risk Program 🧠 | Once foundational controls are in place, start watching for misuse of legitimate access — insider risk often goes undetected the longest. |
| 9️⃣ | Threat Hunting Program 🕵️ | Mature the SOC by actively searching for threats not caught by signatures. Requires good detections, skilled analysts, and time. |
| 🔟 | Cloud Security Program ☁️ | If the organisation uses cloud, evaluate IAM, config management, and logging. Misconfigs are a top cause of breach — don’t skip this. |
| 1️⃣1️⃣ | Third-Party Risk Management Program 🔎 | As vendors increase, so does risk. Triage based on access type, data shared, and business criticality. |
| 1️⃣2️⃣ | Breach & Attack Simulation Program 💥 | Once defences are up, validate them regularly with simulated threats. Helps identify detection gaps and regression. |
| 1️⃣3️⃣ | Digital Forensics & Investigation Program 🧪 | Needed post-incident to support investigations. May be basic early on and grow with need or regulatory requirement. |
| 1️⃣4️⃣ | Data Loss Prevention (DLP) Program 🧬 | Useful for protecting IP and regulated data, but often resource-heavy and noisy. Best implemented after maturity in IR and tooling. |
| 1️⃣5️⃣ | Security Architecture Program 🧰 | A long-term initiative to secure-by-design — often part of a broader transformation effort. Introduce when building new apps or networks. |
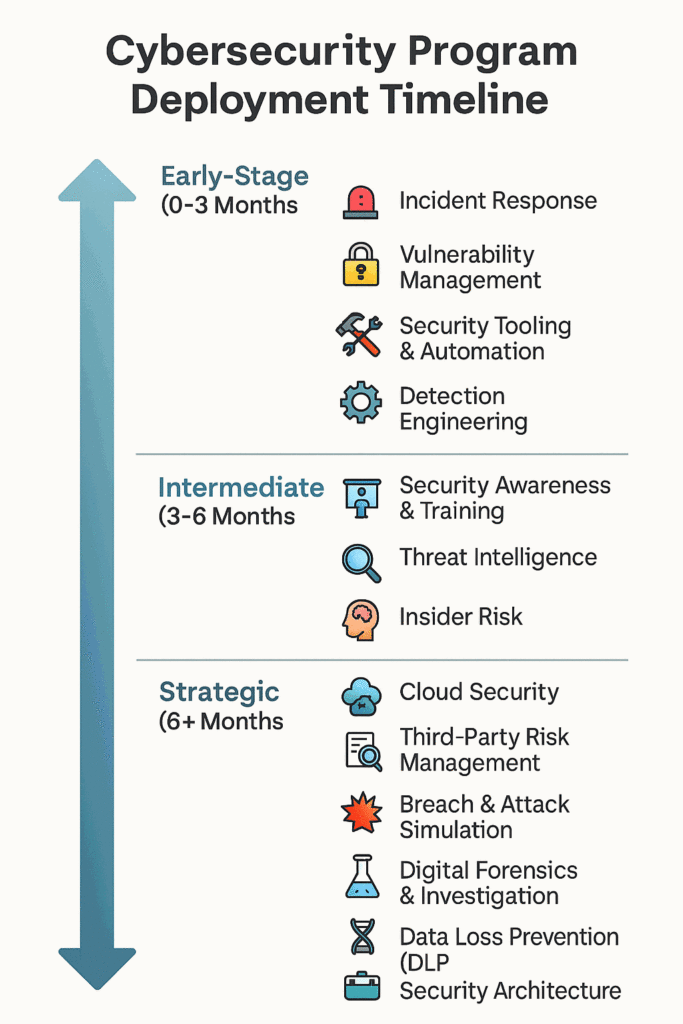
✅ Early-Stage Essentials (First 90 Days)
- Incident Response
- Vulnerability Management
- Tooling/Logging Setup (SIEM, EDR)
- Detection Engineering
- GRC Foundations
🛠 Intermediate Focus (90–180 Days)
- Threat Intelligence
- Insider Risk
- Security Awareness
- Cloud Security Review
🎯 Strategic/Mature Stage (6+ Months)
- Threat Hunting
- BAS
- Third-Party Risk
- DLP & Security Architecture