Contents
- 1 Quantum Computing vs Cybersecurity
- 1.1 Major Cybersecurity Threats
- 1.1.1 RSA Encryption Breakdown
- 1.1.2 Digital Signatures Compromised
- 1.1.3 TLS/SSL Infrastructure
- 1.1.4 Financial Systems
- 1.1.5 Blockchain & Cryptocurrency
- 1.1.6 VPN & Secure Communications
- 1.1.7 Cloud Security
- 1.1.8 Critical Infrastructure
- 1.1.9 Mobile & IoT Security
- 1.1.10 Key Quantum Algorithms Threatening Cybersecurity
- 1.2 Defense Strategies
- 1.3 🧠 Quantum Computing Threats to Cybersecurity
- 1.4 🔐 Why Is This a Threat?
- 1.5 🔐 Real-World Impact
- 1.6 ✅ Summary
Quantum Computing vs Cybersecurity
The Coming Cryptographic Apocalypse
Present Day
Current quantum computers are limited but advancing rapidly. RSA-2048 and ECC still secure, but research accelerating.
2025-2030
Quantum computers may achieve cryptographically relevant capabilities. Time to implement post-quantum cryptography.
2030+
Large-scale quantum computers could break current encryption. Organizations without quantum-safe measures face severe risk.
Major Cybersecurity Threats
RSA Encryption Breakdown
CRITICALShor’s algorithm can factor large integers exponentially faster than classical computers, making RSA encryption obsolete.
90% vulnerability when quantum achievedDigital Signatures Compromised
CRITICALECDSA and DSA signatures become forgeable, breaking authentication and non-repudiation systems worldwide.
85% of current signatures at riskTLS/SSL Infrastructure
CRITICALHTTPS connections become interceptable, breaking the security foundation of the modern internet.
80% of web traffic vulnerableFinancial Systems
CRITICALBanking, cryptocurrency, and payment systems face complete cryptographic failure and potential collapse.
95% of financial crypto vulnerableBlockchain & Cryptocurrency
HIGHBitcoin and most cryptocurrencies use ECDSA signatures, making them vulnerable to quantum attacks.
75% of blockchain systems at riskVPN & Secure Communications
HIGHCorporate VPNs, secure messaging, and encrypted communications become transparent to quantum adversaries.
70% of VPN protocols vulnerableCloud Security
HIGHCloud storage encryption, API security, and multi-tenant isolation mechanisms face quantum threats.
65% of cloud encryption at riskCritical Infrastructure
HIGHPower grids, healthcare systems, and government networks relying on current encryption face exposure.
60% of infrastructure crypto vulnerableMobile & IoT Security
MEDIUMDevice authentication, secure boot, and encrypted communications in billions of devices become compromised.
55% of device security affectedKey Quantum Algorithms Threatening Cybersecurity
Shor’s Algorithm: Factors large integers and computes discrete logarithms efficiently, breaking RSA, DH, and ECC.
Grover’s Algorithm: Provides quadratic speedup for searching, effectively halving symmetric key security (AES-256 becomes AES-128 equivalent).
Quantum Period Finding: Core component enabling cryptanalysis of many public-key systems.
Defense Strategies
Post-Quantum Cryptography
NIST-standardized algorithms like CRYSTALS-Kyber, CRYSTALS-Dilithium, and FALCON provide quantum-resistant security.
Quantum Key Distribution
Physics-based security using quantum mechanics principles for unbreakable key exchange.
Crypto-Agility
Design systems to easily swap cryptographic algorithms as new threats and solutions emerge.
Hybrid Security Models
Combine classical and post-quantum algorithms during the transition period for defense-in-depth.
Early Migration Planning
Begin transitioning critical systems now, before quantum computers achieve cryptographic relevance.
Quantum-Safe Standards
Implement emerging standards and protocols designed to withstand quantum attacks.
Immediate Actions for Organizations
- Inventory Current Cryptography: Catalog all cryptographic implementations across your organization
- Risk Assessment: Prioritize systems based on data sensitivity and quantum threat timeline
- Pilot Programs: Test post-quantum algorithms in non-critical environments
- Vendor Engagement: Work with suppliers to understand their quantum-readiness roadmaps
- Training Programs: Educate security teams on post-quantum cryptography
- Policy Updates: Revise security policies to include quantum threat considerations
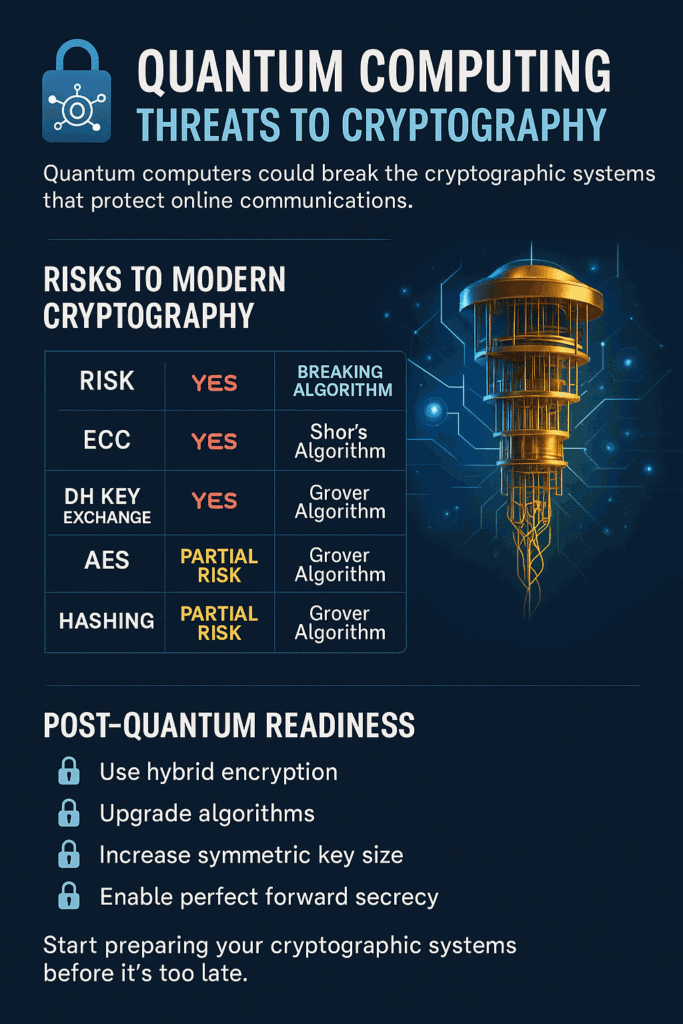
🧠 Quantum Computing Threats to Cybersecurity
Quantum computing is no longer science fiction—it’s a rapidly advancing field that poses real threats to today’s encryption standards. While quantum computers promise breakthroughs in fields like chemistry and logistics, they also threaten the cryptographic backbone of modern security.
⚛️ What Is Quantum Computing?
Unlike classical computers that use bits (0 or 1), quantum computers use qubits, which can be both 0 and 1 at once (superposition). They also leverage entanglement to perform complex calculations in parallel.
🚀 Quantum algorithms can solve certain problems exponentially faster than classical ones.
🔐 Why Is This a Threat?
Modern cybersecurity relies heavily on mathematically hard problems that take classical computers thousands of years to solve. Quantum computers could solve these in minutes using specialised algorithms:
| Encryption Type | Threat from Quantum | Algorithm Broken |
|---|---|---|
| RSA (2048+) | ✅ Yes | Shor’s Algorithm |
| ECC (e.g. Curve25519) | ✅ Yes | Shor’s Algorithm |
| DH Key Exchange | ✅ Yes | Shor’s Algorithm |
| AES-128 | ⚠️ Partial Risk | Grover’s Algorithm (halves security) |
| SHA-256 (Hashing) | ⚠️ Partial Risk | Grover’s Algorithm |
🧪 Key Algorithms That Break Modern Crypto
- Shor’s Algorithm – efficiently factors large primes (used in RSA, ECC, DH)
- Grover’s Algorithm – speeds up brute-force attacks on symmetric ciphers (like AES) and hashing (SHA)
🔐 Real-World Impact
- TLS/HTTPS: A quantum attacker could decrypt traffic if they capture it today and crack it later (known as “harvest now, decrypt later”)
- Digital Signatures: Could be forged once public keys are reverse-engineered
- Blockchain: Public-key-based wallets (like Bitcoin/Ethereum) could be vulnerable if quantum systems advance faster than mitigation
🛡 What Can We Do? (Post-Quantum Readiness)
| Step | Action |
|---|---|
| Use Hybrid TLS | Combine traditional + post-quantum key exchange (e.g. Kyber + ECDHE) |
| Upgrade Algorithms | Move toward PQ-safe standards like Kyber, Dilithium, SPHINCS+ |
| Larger Symmetric Keys | Use AES-256 instead of AES-128 to mitigate Grover’s threat |
| Avoid long-term key reuse | Use short-lived session keys (perfect forward secrecy) |
| Start crypto inventory | Map where RSA/ECC is used in your systems |
🌍 Who’s Leading the Defence?
- NIST is standardising post-quantum cryptography (PQC)
- Finalists: Kyber (encryption), Dilithium (signatures), Falcon
- TLS 1.3 can support hybrid key exchanges (e.g. Cloudflare, Google testing Kyber)
- VPN vendors, browsers, and OS vendors are preparing hybrid-ready stacks
❗ Not All Risks Are Immediate
| Sector | Timeline of Risk |
|---|---|
| Military & intelligence | Already preparing (classified systems) |
| Financial sector | Preparing in 3–5 years |
| Consumer-grade apps | Likely safe until ~2030 |
🕒 But encrypted data stolen today may be decrypted tomorrow—start preparing now.
✅ Summary
| Crypto Task | Vulnerable? | PQ-Safe Alternatives |
|---|---|---|
| RSA / ECC | ✅ Yes | Kyber, Dilithium |
| AES / SHA-256 | ⚠️ Partial | AES-256, SHA-3, BLAKE3 |
| TLS / HTTPS | ✅ Yes | TLS 1.3 with hybrid KEM |
| Digital Signatures | ✅ Yes | SPHINCS+, Dilithium |
📎 Additional Resources
🔐 The post-quantum future is coming. Start preparing your crypto infrastructure before it’s too late.