Contents
⚔️ Cybersecurity Team Roles Explained: Red, Blue & Purple Teams
In modern cybersecurity, defence is no longer a passive role. Organisations need active strategies to test, detect, and improve their resilience against increasingly sophisticated threats.
That’s where the Red, Blue, and Purple Teaming model comes in—a dynamic approach that blends attack simulation, defence, and collaboration to harden security posture.
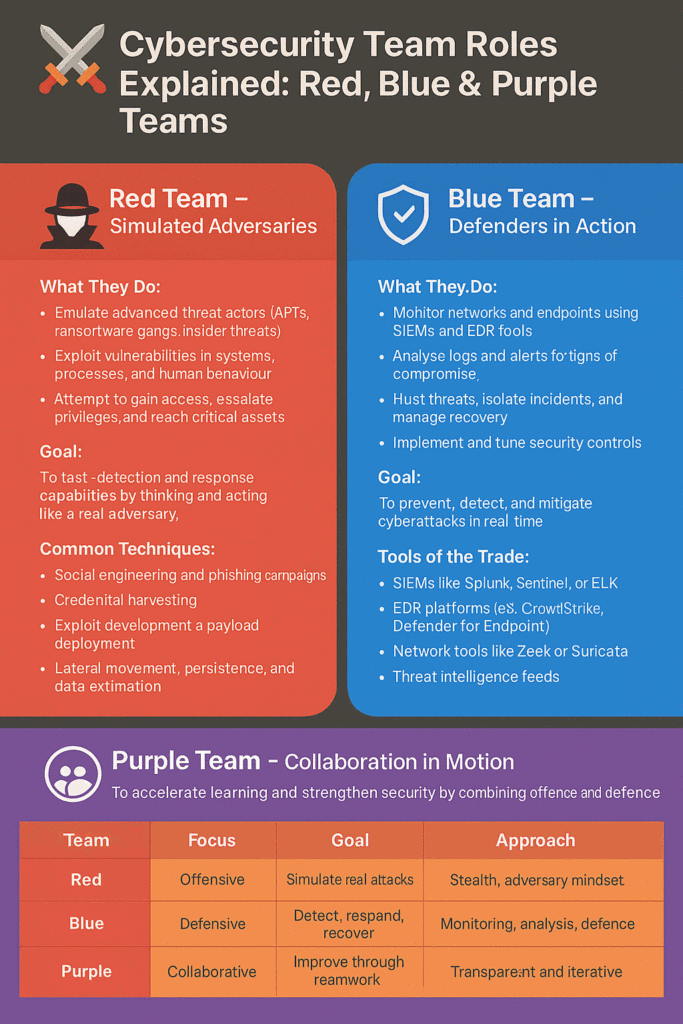
🔴 Red Team – Simulated Adversaries
Red Teams operate offensively, simulating real-world attacks to test how well an organisation can withstand threats.
🔍 What They Do:
- Emulate advanced threat actors (APTs, ransomware gangs, insider threats)
- Exploit vulnerabilities in systems, processes, and human behaviour
- Attempt to gain access, escalate privileges, and reach critical assets
- Test physical security, phishing resilience, and detection evasion
🧪 Goal:
To test detection and response capabilities by thinking and acting like a real adversary.
🧰 Common Techniques:
- Social engineering and phishing campaigns
- Credential harvesting
- Exploit development and payload deployment
- Lateral movement, persistence, and data exfiltration
📌 Red Teams show you where you’re vulnerable—before a real attacker does.
🔵 Blue Team – Defenders in Action
Blue Teams are your security defenders. They work continuously to monitor, detect, respond to, and recover from cyber threats.
🛠️ What They Do:
- Monitor networks and endpoints using SIEMs and EDR tools
- Analyse logs and alerts for signs of compromise
- Hunt threats, isolate incidents, and manage recovery
- Implement and tune security controls
- Educate staff on secure behaviour
🎯 Goal:
To prevent, detect, and mitigate cyberattacks in real-time.
🧰 Tools of the Trade:
- SIEMs like Splunk, Sentinel, or ELK
- EDR platforms (e.g. CrowdStrike, Defender for Endpoint)
- Network tools like Zeek or Suricata
- Threat intelligence feeds
- Scripting for automation (e.g. PowerShell, Python)
📌 Blue Teams are the guardians of your digital environment.
🟣 Purple Team – Collaboration in Motion
Purple Teams bridge the gap between Red and Blue teams. Rather than working in isolation, both sides collaborate in structured exercises to share insights, improve detection, and strengthen defences.
🤝 What They Do:
- Coordinate simulated attacks with transparent communication
- Help Blue Teams understand Red Team tactics and TTPs
- Validate logging and detection coverage
- Tune SIEM and alerting rules based on real attack simulations
- Run adversary emulation exercises using frameworks like MITRE ATT&CK
🎯 Goal:
To accelerate learning and strengthen security by combining offence and defence.
🧰 Example Tools:
- Atomic Red Team (attack simulation)
- MITRE ATT&CK Navigator
- Sigma rules (for SIEM tuning)
- SOAR platforms like Splunk SOAR or TheHive
📌 Purple Teams turn lessons into improvements—fast.
🧠 Red vs Blue vs Purple – Summary Table
| Team | Focus | Goal | Approach |
|---|---|---|---|
| Red | Offensive | Simulate real attacks | Stealth, adversary mindset |
| Blue | Defensive | Detect, respond, recover | Monitoring, analysis, defence |
| Purple | Collaborative | Improve through teamwork | Transparent and iterative |
✅ Why It All Matters
Together, these teams form a cybersecurity ecosystem. Red Teams test, Blue Teams defend, and Purple Teams ensure everyone learns and improves.
🔐 You don’t just need defences—you need to know they work. That’s where teamwork wins.